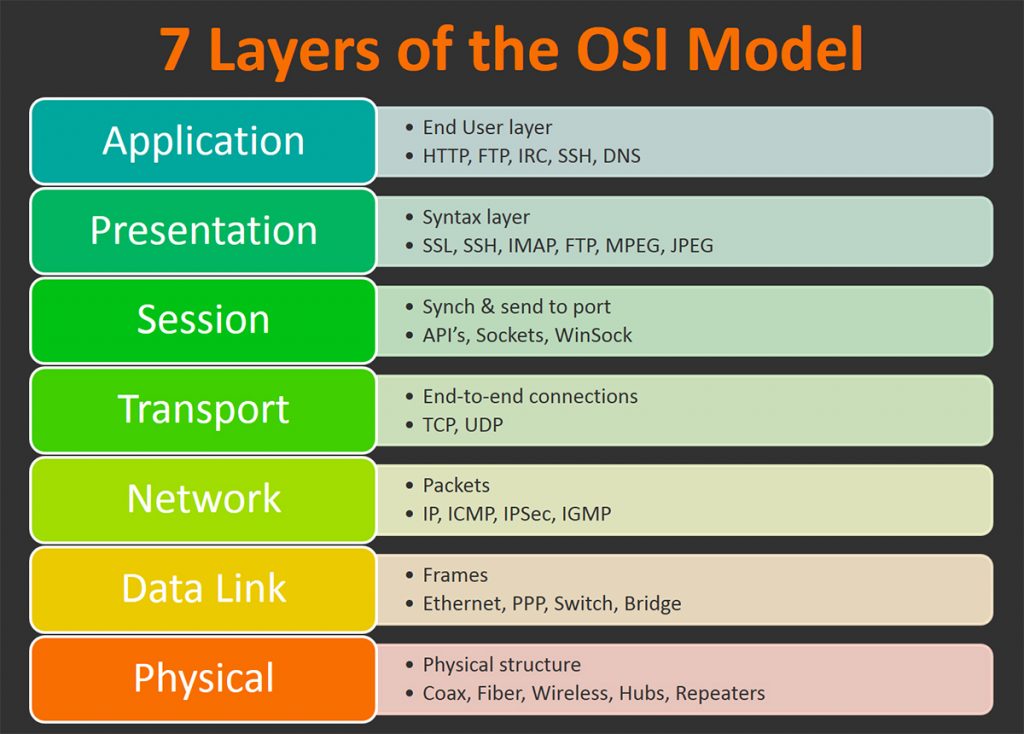
The Open Systems Interconnection (OSI) model is a framework used to understand how different networking protocols and technologies interact with each other. It was developed in the 1970s by the International Organization for Standardization (ISO) to promote network interoperability and facilitate communication between devices from different manufacturers.
The OSI model consists of seven layers, each with its own specific function, and provides a structured approach to designing, implementing, and troubleshooting networks. In this article, we will delve into each layer of the OSI model, its purpose, and how it contributes to the overall functioning of a network.
Layer 1: Physical Layer
The physical layer is the lowest layer in the OSI model and deals with the physical connections and signaling between devices. It defines the specifications for the cables, connectors, and other hardware components that are used to connect devices in a network.
The physical layer, located at the bottom of the OSI model, manages the physical connections and signaling mechanisms among devices
Purpose of Physical Layer
The primary purpose of the physical layer is to ensure that data can be transmitted reliably over the physical medium. It handles tasks such as encoding, modulation, and synchronization, which are essential for successful data transmission.
One of the key functions of the physical layer is to convert digital signals into analog signals that can be sent over a physical medium such as copper wires or fiber optic cables. It also defines the speed at which data is transmitted, known as the data rate or bandwidth.
Components of Physical Layer
The physical layer comprises various components that work together to establish and maintain a physical connection between devices. These include:
Cables and Connectors
Cables and connectors are used to physically connect devices in a network. There are several types of cables available, including coaxial, twisted pair, and fiber optic cables, each with its own advantages and disadvantages.
For example, coaxial cables are commonly used for cable television and high-speed internet connections, while twisted pair cables are used for Ethernet networks. Fiber optic cables, on the other hand, are known for their high bandwidth and resistance to electromagnetic interference.
Similarly, different types of connectors are used to terminate these cables, such as RJ-45 connectors for twisted pair cables and ST or SC connectors for fiber optic cables.
Hubs
Hubs are simple devices that operate at the physical layer and enable multiple devices to connect to a network. They work by receiving data from one device and forwarding it to all other connected devices. However, they do not have any intelligence to filter or manage network traffic, making them inefficient and obsolete in modern networking.
Repeaters
Repeaters are used to extend the reach of a network by regenerating and amplifying signals as they pass through. They are essential when there is a need to transmit data over longer distances, as signals tend to degrade and weaken the farther, they travel.
Common Issues with Physical Layer
As the physical layer deals with the physical connectivity between devices, any issues at this layer can cause disruptions in the entire network. Some common problems that can occur at the physical layer include:
- Faulty Cables: Damaged or faulty cables can result in poor network performance, signal loss, or complete network outage.
- Loose Connections: Poorly terminated or loose connections can lead to intermittent connectivity issues and signal loss.
- Electromagnetic Interference (EMI): EMI can disrupt the communication between devices and distort signals, leading to data corruption and transmission errors.
- Crosstalk: Crosstalk occurs when signals from one cable interfere with those of another, causing data errors and network congestion.
- Incorrect Bandwidth: If the bandwidth of a cable is insufficient to handle the amount of data being transmitted, it can result in network slowdowns and packet loss.
Layer 2: Data Link Layer
The data link layer is responsible for establishing, maintaining, and terminating connections between devices in a network. It ensures error-free transmission of data by detecting and correcting errors that may occur during data transfer.
Purpose of Data Link Layer
The primary purpose of the data link layer is to provide a reliable and error-free connection between two devices. It achieves this by implementing flow control mechanisms, such as buffer management and packet sequencing, and error detection and correction techniques, such as checksums and acknowledgments.
Components of Data Link Layer
The data link layer comprises two sublayers: the Media Access Control (MAC) sublayer and the Logical Link Control (LLC) sublayer.
MAC Sublayer
The MAC sublayer is responsible for controlling access to the physical medium and determining when devices can transmit data. It uses protocols such as Carrier Sense Multiple Access/Collision Detection (CSMA/CD) or Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) to prevent data collisions between devices.
LLC Sublayer
The LLC sublayer serves as an interface between the data link layer and higher-level protocols. It ensures reliable communication by implementing error-checking and flow control mechanisms and provides logical addressing to uniquely identify devices on a network.
Common Issues with Data Link Layer
Problems at the data link layer can cause disruptions in the communication between devices, resulting in poor network performance and data loss. Some common issues include:
- Duplex Mismatch: When devices on a network have different duplex settings, it can lead to collisions and dropped packets.
- Address Resolution Protocol (ARP) Spoofing: ARP spoofing is a form of cyber-attack where the attacker sends falsified ARP messages to a device to redirect traffic to a different IP address.
- Frame Errors: Frame errors occur when there are issues with the physical layer, causing data corruption and transmission errors.
- Data Collisions: Data collisions happen when two or more devices transmit data simultaneously, resulting in lost or corrupted data.
- Misconfigured Protocols: Incorrectly configured protocols can cause issues with data transfer, leading to performance degradation and network slowdowns.
Layer 3: Network Layer
The network layer is responsible for routing packets across multiple networks, allowing devices to communicate with each other even if they are not directly connected. It also ensures that packets reach their intended destination by selecting the best path and avoiding congested areas of the network.
The network layer handles the routing of packets across various networks, enabling devices to communicate with each other regardless of direct connections
Purpose of Network Layer
The primary purpose of the network layer is to provide logical addressing and routing services to enable communication between different networks. It implements protocols such as Internet Protocol (IP), which assigns a unique IP address to each device on a network, and Routing Information Protocol (RIP) or Open Shortest Path First (OSPF) to determine the best path for packet delivery.
Components of Network Layer
The network layer comprises various components that work together to route packets and maintain connectivity between devices.
Routers
Routers are essential devices that operate at the network layer and are responsible for forwarding packets across networks. They use IP addresses to identify devices and determine the most efficient route for data transmission.
Routing Tables
Routing tables contain information about the routes that a router uses to forward packets. They help routers select the best path for data transmission based on factors such as cost, congestion, and reliability.
Gateways
Gateways are devices that connect different types of networks, such as a local area network (LAN) and a wide area network (WAN). They translate different protocols, such as IPX/SPX and TCP/IP, to enable communication between networks.
Common Issues with Network Layer
Problems at the network layer can cause significant disruptions in the communication between devices, resulting in network outages and data loss. Some common issues include:
- IP Address Conflicts: If two devices have the same IP address, it can lead to conflicts and dropped packets.
- Incorrect Routing Tables: Incorrect routing tables can cause packets to take longer routes or get stuck in a loop, leading to increased latency and network congestion.
- Network Congestion: When there is an increase in network traffic, it can cause congestion, resulting in slow data transfer and delayed packets.
- Denial of Service (DoS) Attacks: DoS attacks involve flooding a network with traffic, causing congestion and preventing legitimate data from reaching its destination.
- Incorrectly Configured Firewalls: Improperly configured firewalls can block legitimate traffic, preventing devices from communicating with each other.
Layer 4: Transport Layer
The transport layer is responsible for ensuring that data is delivered reliably and accurately between end-to-end devices. It breaks down large data streams into smaller segments and reassembles them at the receiving end, providing error checking and flow control mechanisms to ensure data integrity.
Purpose of Transport Layer
The primary purpose of the transport layer is to ensure end-to-end data delivery by providing reliable and ordered delivery of data packets. It also manages communication sessions between devices and controls the flow of data to prevent congestion and packet loss.
Components of Transport Layer
The transport layer comprises two sublayers: the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP).
TCP
TCP is the most widely used transport protocol and provides reliable, ordered, and error-checked data delivery. It establishes a connection between devices before transmission and ensures that all data is received correctly and in the correct order.
UDP
UDP is a connectionless transport protocol that does not provide any guarantees for reliable delivery or packet ordering. It is typically used for real-time applications, such as video and voice conferencing, where the delay caused by error checking would be unacceptable.
Common Issues with Transport Layer
Problems at the transport layer can affect the end-to-end communication between devices, leading to data corruption and loss of connectivity. Some common issues include:
- Congestion Control: Without proper congestion control mechanisms, an increase in network traffic can cause dropped packets and network slowdowns.
- Connection Timeout: If a connection is idle for too long, it may time out and be terminated, resulting in lost data.
- Out-of-Order Packets: If packets arrive at the receiving end out of order, it can cause delays and prevent data from being reassembled correctly.
- Fragmentation: In some cases, data packets may need to be fragmented due to differing maximum transmission unit (MTU) sizes between networks. However, if not done correctly, fragmentation can lead to packet loss and increased latency.
- TCP SYN Flood Attacks: TCP SYN flood attacks involve overwhelming a device with requests to establish connections, causing it to become unresponsive and preventing legitimate connections from being established.
Layer 5: Session Layer
The session layer is responsible for establishing, managing, and terminating sessions between devices. It enables devices to establish a connection and pass data between them, providing additional security and error recovery mechanisms to ensure reliable data transfer.
The session layer’s role includes initiating, overseeing, and concluding sessions between devices
Purpose of Session Layer
The primary purpose of the session layer is to establish and manage communication sessions between devices. It provides mechanisms to initiate, maintain, and terminate sessions, ensuring that data transfer between devices is secure and reliable.
Components of Session Layer
The session layer comprises various components, including:
Session Establishment Protocols
Session establishment protocols, such as NetBIOS, are used to establish a session between devices by exchanging information about the type of services they offer and the protocols they support.
Session Maintenance Protocols
Session maintenance protocols, such as Remote Procedure Call (RPC), are used to keep a session alive by exchanging packets between devices at regular intervals. If there is no activity for a specified period, the session may be terminated.
Session Termination Protocols
Session termination protocols, such as SMB/CIFS, are used to terminate a session between devices once data transfer is complete.
Common Issues with Session Layer
Problems at the session layer can cause disruptions in the communication between devices and lead to failed or aborted sessions. Some common issues include:
- Session Hijacking: Session hijacking is a type of cyber attack where an attacker gains unauthorized access to a session by stealing the session ID or using other methods.
- Session Timeout: If a session is idle for too long, it may timeout and be terminated, leading to lost data.
- Dropped Packets: If packets are dropped during data transfer, it may cause delays and prevent the session from being maintained correctly.
- Protocol Mismatch: If devices do not support the same protocols, it may result in failed sessions and prevent data transfer.
Layer 6: Presentation Layer
The presentation layer is responsible for formatting, compressing, and encrypting data for transmission. It ensures that data is presented in a format that can be understood by both the sender and receiver and provides mechanisms to compress and secure data to reduce the amount of data transmitted over the network.
Purpose of Presentation Layer
The primary purpose of the presentation layer is to ensure that data is presented in a format that can be understood by both the sender and receiver. It also provides mechanisms to compress and secure data to optimize bandwidth and protect sensitive information.
Components of Presentation Layer
The presentation layer comprises various components, including:
Data Formatting
Data formatting involves converting data into a format that can be understood by both the sender and receiver. This includes translating character sets, such as ASCII or Unicode, and ensuring that data is in the correct order.
Data Compression
Data compression reduces the size of data to optimize bandwidth usage. It involves removing redundant information from data streams to decrease the amount of data transmitted over the network.
Data Encryption
Data encryption ensures that sensitive information is protected from unauthorized access during transmission. It uses algorithms, such as Advanced Encryption Standard (AES), to scramble data, making it unreadable to anyone without the correct decryption key.
Common Issues with Presentation Layer
Problems at the presentation layer can cause issues with data formatting, transmission, and security, leading to data loss and security breaches. Some common issues include:
- Incompatible Data Formats: If devices do not support the same data formats, it may result in data being lost or displayed incorrectly.
- Poorly Compressed Data: Improperly compressed data may be corrupted during transmission, leading to data loss and errors.
- Weak Encryption Algorithms: If weak encryption algorithms are used, it may make data vulnerable to attacks and compromise its confidentiality.
- Misconfigured Encryption: If encryption is misconfigured, it may result in data being transmitted without encryption, posing a security risk.
Layer 7: Application Layer
The application layer is the topmost layer of the OSI model and is responsible for providing services to applications and end-users. It enables devices to communicate with different types of applications, such as web browsers, email clients, and file transfer protocols.
Purpose of Application Layer
The primary purpose of the application layer is to enable communication between devices and applications. It provides protocols, such as Hypertext Transfer Protocol (HTTP) and Simple Mail Transfer Protocol (SMTP), to facilitate data transfer between devices.
Components of Application Layer
The application layer comprises various components, including:
Application Protocols
Application protocols, such as HTTP, SMTP, and File Transfer Protocol (FTP), are used to enable communication between devices and applications. They define how data is formatted, transmitted, and received by a particular application.
Application Services
Application services provide specific functionality to applications, such as authentication, authorization, and access control. They ensure that only authorized users have access to specific resources and services.
Application Interfaces
Application interfaces allow applications to communicate with other applications or services. These can include APIs, web services, and remote procedure calls.
Common Issues with Application Layer
Problems at the application layer can cause disruptions in the communication between devices and applications, leading to failed connections and data loss. Some common issues include:
- Incompatible Applications: If two applications do not support the same protocols or formats, it may result in failed connections and lost data.
- Denial of Service (DoS) Attacks: DoS attacks targeting specific applications, such as email servers or web servers, can cause service disruptions and prevent legitimate access to applications.
- Resource Exhaustion: If an application consumes too many resources, it may affect the performance of other applications and lead to service disruptions.
- Invalid Requests: If an application receives invalid requests, it may lead to errors and prevent successful communication.
Conclusion
In summary, the OSI model provides a structured approach to understanding how different networking protocols and technologies interact with each other. By dividing the complex process of data transmission into seven layers, it enables network administrators to identify and troubleshoot issues more efficiently.
Each layer of the OSI model has a specific purpose and contributes to the overall functioning of a network. Understanding the function of each layer and the common issues that can occur at each level is crucial for designing, implementing, and maintaining a reliable and efficient network. By following the OSI model, network professionals can ensure that their networks are secure and perform optimally for their intended purpose.
